14. NIST Cybersecurity Framework (CSF) Exercise
NIST Cybersecurity Framework (CSF) Exercise
The NIST Cybersecurity Framework (CSF) Core includes five high level functions: Identify, Protect, Detect, Respond, and Recovery and 23 Categories that are split across the five Functions. The image below depicts the Framework Core's Functions and Categories.
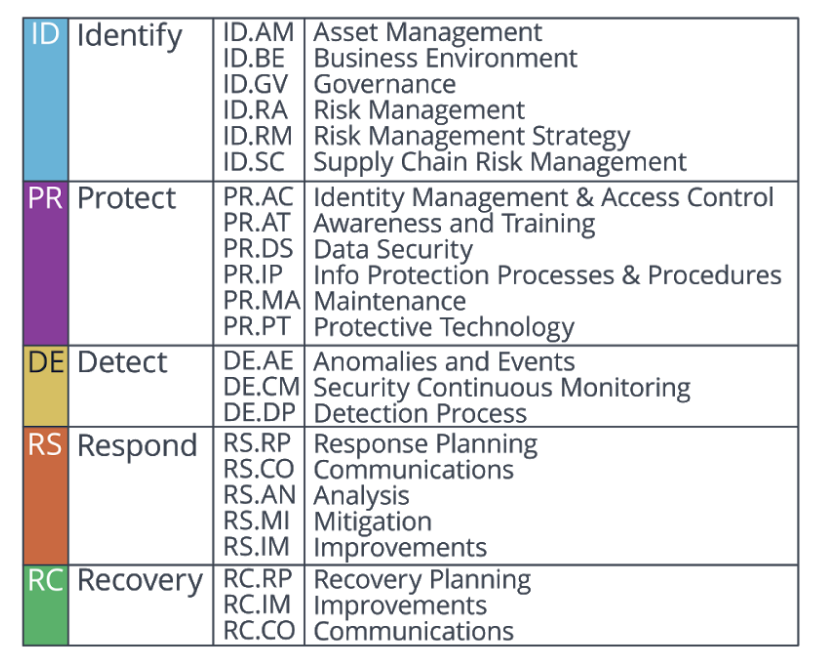
Identify Function
QUESTION:
The Identify Function assists in developing an organizational understanding in managing cybersecurity risk to systems, people, assets, data, and capabilities. Understanding the business context, the resources that support critical functions, and the related cybersecurity risks enable an organization to focus and prioritize its efforts, consistent with its risk management strategy and business needs.
List at least three examples of the Identify Function.
ANSWER:
Examples of outcome Categories within the Identify Function include:
- Identifying physical and software assets within the organization to establish the basis of an Asset Management program
- Identifying the Business Environment the organization supports including the organization's role in the supply chain and the organization's place in the critical infrastructure sector
- Identifying cybersecurity policies established within the organization to define the Governance program as well as identifying legal and regulatory requirements regarding the cybersecurity capabilities of the organization
- Identifying asset vulnerabilities, threats to internal and external organizational resources, and risk response activities as a basis for the organization's Risk Assessment
- Identifying a Risk Management Strategy for the organization including establishing risk tolerances
- Identifying a Supply Chain Risk Management strategy including priorities, constraints, risk tolerances, and assumptions used to support risk decisions associated with managing supply chain risks
Answers found at https://www.nist.gov/cyberframework/online-learning/five-functions
Protect Function
QUESTION:
The Protect Function outlines appropriate safeguards to ensure delivery of critical infrastructure services. The Protect Function supports the ability to limit or contain the impact of a potential cybersecurity event.
List at least three examples of the Protect Function.
ANSWER:
Examples of outcome Categories within the Protect Function include:
- Protections for Identity Management and Access Control within the organization including physical and remote access
- Empowering staff within the organization through Awareness and Training including role based and privileged user training
- Establishing Data Security protection consistent with the organization’s risk strategy to protect the confidentiality, integrity, and availability of information
- Implementing Information Protection Processes and Procedures to maintain and manage the protection of information systems and assets
- Protecting organizational resources through Maintenance, including remote maintenance, activities
- Managing Protective Technology to ensure the security and resilience of systems and assists are consistent with organizational policies, procedures, and agreements
Answers found at https://www.nist.gov/cyberframework/online-learning/five-functions
Detect Function
QUESTION:
The Detect Function describes suitable actions to recognize the existence of a cybersecurity event. The Detect Function allows the identification of cybersecurity events.
List at least three examples of the Detect Function.
ANSWER:
Examples of categories within the Detect Function include:
- Ensuring Anomalies and Events are identified, and their possible effects are analyzed
- Implementing Security Continuous Monitoring capabilities to watch for cybersecurity events and verify the usefulness of defensive methods including network and physical activities
- Maintaining Detection Processes to provide awareness of anomalous events
Answers found at https://www.nist.gov/cyberframework/online-learning/five-functions